Hack the Box - Trick
- BlueDolphin
- Nov 2, 2022
- 6 min read
Enumeration

Summary
This machine initially required subdomain enumeration which opened the door for a new attack surface that was exploited with SQL injection using SQL Map. This provided user credentials from the user database which allowed for a login on the target web application. Further subdomain enumeration lead to a new web site and attack surface where we took advantage of directory traversal tailored to bypass a web application firewall.
This allowed for the extraction of a SSH key which was used to gain user level access to the Host. Performing initial enumeration uncovered the fail2ban application that had a group permissions that gave us folder access to the actions.d folder. This is an important folder called by fail2ban when taking restrictive action against an offender. We were able to modify a script that would fire when a user was unbanned and this allowed for RCE to root.
Tools used
WFUZZ
SQLMAP
Burpsuite
inpeas
Auto recon
Fail2ban
dig
whatweb
Processes/Techniques
Sub domain enumeration
SQL injection automation
Request proxying
Internal enumeration automation
External enumeration automation
Permissions abuse
DNS zone transfer
Enumeration
Starting off with Autorecon we notice five ports, TCP 22,25,53,80 and UPD 53.
We receive a DNS recon error when enumerating port 53 over UDP as we did not have the domain name. This again triggered on port 53 over TCP.
Auto Recon

Image - Autorecon
Basic Nmap Scan
Running our standard nmap scan reveals 4 ports.

Image - nmap results
Port 25 - SMTP enumeration login credentials found at 10.129.34.40:25/vrfy

Image - SMTP enumeration results
Port 53 - DNS recon

Image - Directory discovery
Port 80 - directory busting

Image - Directory discovery results
Port 80 - What web
└─$ cat tcp_80_http_whatweb.txt
WhatWeb report for http://10.129.34.40:80
Status : 200 OK
Title : Coming Soon - Start Bootstrap Theme
IP : 10.129.34.40
Country : RESERVED, ZZ
Summary : Bootstrap, HTML5, HTTPServer[nginx/1.14.2], nginx[1.14.2], Script
Detected Plugins:
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : nginx/1.14.2 (from server string)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.14.2
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.14.2
Date: Tue, 11 Oct 2022 23:00:36 GMT
Content-Type: text/html
Last-Modified: Wed, 23 Mar 2022 16:34:04 GMT
Transfer-Encoding: chunked
Connection: close
ETag: W/"623b4bfc-1568"
Content-Encoding: gzip
Re-Enumerate
We add trick.htb to our /etc/hosts folder and re-run auto recon.

Image - etc/hosts file
Reviewing the new results from Auto recon that have resulted from the DNS enumeration utilizing the DIG tool, across the FQDN name, yielded different results. We notice 2 new subdomains,.
preprod-payroll.trick.htb
root.trick.htb

Image - DNS DIG results
Web Enumeration
The website is totally empty and nothing stands out as a point of interest beyond an email address form, which offered nothing upon initial enumeration.

Image - Website landing page
Browsing to the root.tick.htb FQDN shows the same landing page and attack surface.

Image - root.trick.htb over http
We browse to the preprod-payroll.trick.htb FQDN and receive a new landing page with a new attack surface to enumerate. Trying default credentials lead nowhere, so I pivoted to SQLmap for further enumeration.

Image - preprod-payroll.trick.htb
SQLMAP
SQLmap has a fantastic function, where you can capture a web request and feed this to SQLMap. We were able to use burpsuite to intercept the login POST request, and save this locally feeding it to SQLMap. SQLMap was able to identify that the POST parameter for the login function was indeed vulnerable to SQL injection.

Image - SQLMap
From here we are able to pivot are initial SQLMap enumeration after learning the target is vulnerable to injection and hosts the mysql database management system. We change our function of SQLMap to reveal the specific database tables hosted on our target with the below command, The results reveal that our target is running 2 tables, an information_schema table which is standard by default, as well as a payroll_db table.
sqlmap -r request --dbms mysql --dbs-r - calls a requests file with the URL and target parameter
--dbms - specifies a database management system
--dbs - calls the database enumeration function

Image - SQLMap
From here we are able to again pivot and target the specific tables within the payroll_db database. The results provide us with a dozen tables that we can start to dive in to with the intent to find sensitive information to help us establish a foothold on the target.
sqlmap -r request --dbms mysql -D payroll_db --tables-r - calls a requests file with the URL and target parameter
--dbms - specifies a database management system
-D - Specifies a known database
--tables - calls the table enumeration function

Image - SQLMap
After enumerating the dozen tales, we find in the last table labled "users" there are credentials for a user.
sqlmap -r request --dbms mysql -D payroll_db -T users --dump-r - calls a requests file with the URL and target parameter
--dbms - specifies a database management system
-D - Specifies a known database
-T - Specifies a known table

Image - Credentials found SuperGucciRainbowCake | Enemigosss
Initial foothold
We are able to login to the proprod webpage with those credentials found from our SQLMap enumeration of the users table in the payroll_db database.

Image - webapp login page
Web App Authenticated Enumeration
After looking around the web application it appears there is nothing clearly vulnerable. Pivoting into sub domain enumeration reveals there is a "marketing" subdomain.
wfuzz -c -w /usr/share/spiderfoot/spiderfoot/dicts/subdomains-10000.txt -u http://10.129.144.30 -H 'Host: preprod-FUZZ.trick.htb'

Image - Domain fuzzing
Browsing to preprod-marketing.trick.htb reveals a new landing web page.

Image - preprod-marketing.trick.htb
Inspecting the source code of the page reveals php queries from the index.php page. This is a potential target for directory traversal or command injection.

Image - page source code
Attempting to conduct directory traversal and command injection does not initially work. However when we take our directory traversal attempts to another layer by using payloads found on "all things payloads" we can use strings that are designed to bypass web application firewalls. Our desired payload is ..././ which tricks the WAF. The reason for this, the WAF looks for malicious patterns which are identified as ../ a natural part of a directory traversal. However, the vulnerability is in that the WAF removes the ../ pattern so when we pass the payload, the WAF removes the ..././ the characters highlighted in green leaving only the ../ characters behind which are passed to the backend.

Image - payload all things
Our target payload is successful in bypassing the WAF and we are able to confirm this be outputting the contents of the /etc/passwd file.

Image - contents of /etc/passwd
Looking around on the target host we eventually find in user Michaels directory, a ssh/id_rsa key.

Image - .ssh/id_rsa
From here we copy the RSA key and the formatting is off. So we leverage the curl command to download it in proper format. From here we

Image - Access as user Michael over SSH
Root
We start off our path to obtain elevated privileges with the linpeas script as usual.

Image - Linpeas results showing /etc/fail2ban/action.d
Reviewing our sudo permissions we learn that the user can run /etc/init.d/fail2bain restart as root.

Image - sudo permissions
Reviewing the fail2ban directory provides the additional files including our jail.conf file. This file stores standard configuration information for the fial2ban service. Reviewing the file permissions shows something out of place. This is the action.d folder which appears to have the root/security permission.

Image - fail2bain sub directory permissions
Reviewing the group permissions for Michael reveals that he is apart of the security group. From here we start to put the whole picture together.

Image - security groups for Michael
The jail config shows our ban actions for excessive connections.

image - jail.conf
The iptables-multiport.conf describes the actions for banning IP's that violate the connection rules. We can see at the bottom, we have something interesting.
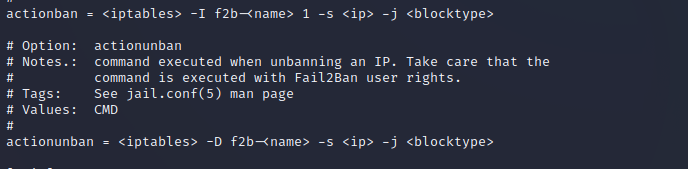
image - iptables-multiport.conf
Lets attempt to fail a connection several times with pspy running.

image - pspy
We see this response upon failure

image - pspy
We can see our command executed, so let's target the flag as our shell is not working. We had to add out command to the actionban and actionunban,

image - pspy
Observed multiport running

image - pspy
It seems like we have to call /bin/bash

image - pspy
Finally I tired changing permissions on /bin/bash with
chmod +s /bin/bash
This then set the SUID permission on bash and we had access as root.


Comments